Resister: A Resilient Interposer Architecture for Chiplet to Mitigate Timing Side-Channel Attacks
By Xinrui Wang 1, Lang Feng 2, Yujie Wang 3, Taotao Xu 3, Yinhe Han 3, and Zhongfeng Wang 1,2
1 Nanjing University, Nanjing, China
2 School of Integrated Circuits, Sun Yat-Sen University, Shenzhen, China
3 Institute of Computing Technology Chinese Academy of Sciences, Beijing, China
Abstract
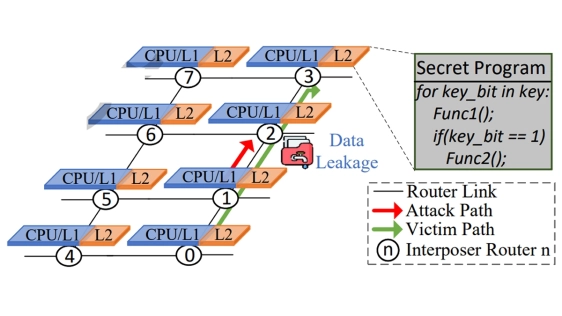
 Chiplet technology has been a hot topic due to its potential for more efficient implementation of large-scale integrated circuits. In chiplet manufacturing, the general-purpose active interposer usually integrates chiplets from different vendors with a typical mesh network. This method of manufacturing is broadly recognized for its cost-efficiency. However, untrusted vendors make the chiplet system vulnerable to security threats such as timing side-channel attacks (TSA) based on network contention information. Even worse, the reliability of each chiplet is usually unknown beforehand to a general-purpose interposer’s manufacturer, so that TSAs can be on arbitrary chiplets at arbitrary time in the manufacturer’s view. To address this challenge, this work first quantitatively analyzes the attack patterns including reinforced styles, based on which, a resilient interposer architecture named Resister is proposed. A hardware defender is designed in every router to globally detect the malicious transaction patterns at runtime, and adaptively detour the transaction packets accordingly for security while maintaining the performance. According to the evaluation of GEM5 on SPEC 2017 and PARSEC benchmarks, Resister can effectively mitigate TSA with only a 1.7% performance overhead.
Chiplet technology has been a hot topic due to its potential for more efficient implementation of large-scale integrated circuits. In chiplet manufacturing, the general-purpose active interposer usually integrates chiplets from different vendors with a typical mesh network. This method of manufacturing is broadly recognized for its cost-efficiency. However, untrusted vendors make the chiplet system vulnerable to security threats such as timing side-channel attacks (TSA) based on network contention information. Even worse, the reliability of each chiplet is usually unknown beforehand to a general-purpose interposer’s manufacturer, so that TSAs can be on arbitrary chiplets at arbitrary time in the manufacturer’s view. To address this challenge, this work first quantitatively analyzes the attack patterns including reinforced styles, based on which, a resilient interposer architecture named Resister is proposed. A hardware defender is designed in every router to globally detect the malicious transaction patterns at runtime, and adaptively detour the transaction packets accordingly for security while maintaining the performance. According to the evaluation of GEM5 on SPEC 2017 and PARSEC benchmarks, Resister can effectively mitigate TSA with only a 1.7% performance overhead.
To read the full article, click here
Related Chiplet
- DPIQ Tx PICs
- IMDD Tx PICs
- Near-Packaged Optics (NPO) Chiplet Solution
- High Performance Droplet
- Interconnect Chiplet
Related Technical Papers
- A Heterogeneous Chiplet Architecture for Accelerating End-to-End Transformer Models
- Gemini: Mapping and Architecture Co-exploration for Large-scale DNN Chiplet Accelerators
- Photonic Chiplet Interconnection via 3D-Nanoprinted Interposer
- ChipletQuake: On-die Digital Impedance Sensing for Chiplet and Interposer Verification
Latest Technical Papers
- Spatiotemporal thermal characterization for 3D stacked chiplet systems based on transient thermal simulation
- Interconnect-Aware Logic Resynthesis for Multi-Die FPGAs
- Scope: A Scalable Merged Pipeline Framework for Multi-Chip-Module NN Accelerators
- Scaling Routers with In-Package Optics and High-Bandwidth Memories
- TDPNavigator-Placer: Thermal- and Wirelength-Aware Chiplet Placement in 2.5D Systems Through Multi-Agent Reinforcement Learning